Product Chakra
Negotiable Min Order Quantity Unit
- Required Quantity
-
- Place of Origin
- Payment Terms
- Negotiable
- Production method
- Negotiable
- Shipping / Lead Time
- Negotiable / Negotiable
- Keyword
- Category
- Computer Software
Apply a video call to the Supplier

Ware Valley Co., Ltd.
- Country / Year Established
-
 South Korea
/
South Korea
/
- Business type
- Others
- Verified Certificate
-
16


| Product name | Product Chakra | Certification | - |
|---|---|---|---|
| Category | Computer Software | Ingredients | - |
| Keyword | - | Unit Size | - |
| Brand name | - | Unit Weigh | - |
| origin | Stock | - | |
| Supply type | - | HS code | - |
Product Information
Database Security Overview
�Understanding the DB security industry paradigm
① From investment and construction to efficient use of resources and security era. In the last 10 years, the main goal of the IT industry was expanding the infra. However, the focus has now shifted, and has become a national task, to develop it in a safe and sound manner. Protection of information assets, no longer simply means the protection of the physical system or software, but encompasses internal security and establishment of security awareness.
As a result, regulations and guides for IT users and solution vendors are being created, in order to guarantee the efficiency and saftey of the information infra. The convenience of information usage and a real-time execution environment has led to various forms of threatening factors. As such ill effects increase, regulations and supervision are expected to be reinforced to secure stability.
Information system related regulations and an IT compliance market are being created, in order to meet such industrial demands.
Compliance demands on firms are expected to increase, and once a regulation is made it will continue to be enforced.
The larger and higher a building rises, the higher the demands of more stringent regulations, such as, provision of estinguishers, emergency staircases, and heliports. Likewise, as society relies more and more on the information system, demands for secure and unfragmented information will arise from outside the corporal environment, leading to the development of relavent solutions. At present, compliance demands on companies have only just begun to arise. However, it is expected that, not only compliance demands on server and storage hardware, system software, application software, but also, demands on IT services integrating hardware and software will increase, in the near future.
② Implementing a real-time monitor, restriction and auditing system for DB operations within a company.
Although there have been various IT related regulations in the past, recent demands have led to more systematic regulations, such as, the Sarbanes-Oxley Act (SOA) of 2002, Basel II by the Bank for International Settlements (BIS), and information security regulation. The SOA was established in response to the Enron, WorldCom accounting scandals of 2001, to ensure transparency in financial statements and disclosures. Such regulations have made it necessary for global corporations, such as, POSCO, to construct an internal restriction system and establish response strategies in advance, for protecting information and managing hazards. In addition, increasing personal information security awareness, and reported cases of leakage of important information(data), have led to a demand for technology to secure such information, and develop a system for system developers and administrator to efficiently manage, monitor, and restrict accesses to information.
Protection of important data and prevention of DB leakage without loading the system, by 100% logging of all real-time monitor, restriction, and accesses to the database under surveillance, and post-analysis of the logged records.
Establishing an information security system in response to IT compliance. Not only is it necessary to establish an internal restriction system, it is also imperative that general security problems be solved, such as, those related to processes, the operation system, document access, database security and backup, in order to fully comply with this regulation.
The importance of not only internal operation system security, but also secure management, restriction, and auditing of the database containing vital company information, is being more and more emphasized.
For efficient database security management, a system for real-time monitor and logging of all DB accesses is needed, in order to apply security restrictions in advance and aquire proof for enforcing regulations.
Product Features & Architecture
The database systems managed by companies are various and the tasks complicated. In a large system which deals with several thousand transitions per second, even a short interval of abnormal operation can cause huge losses. It therefore important to choose a system that will cause 0% damage, when establishing a DB security system for monitoring the database on a real-time basis.
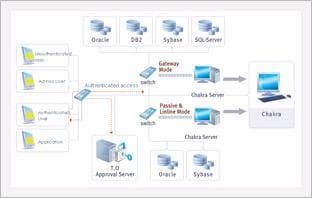
The company's operations must not be affected even when a physical problem occurs in the system under surveillance. Chakra offers a solution for such requirements, enabling real-time monitoring of the database, without needing to access the database. Chakra identifies all tasks requested to the database and by whom, on a real-time basis, enables searching of when, where, and which data, is queried and modified by whom, and supplies the necessary information for troubleshooting when a problem occurs.
| Protection | Real-time monitoring of all accesses to the database (Host, Application, User, ID, time) and the contents of the task (SQL type and etc.) |
| In the case of a violation to an established security policy, immediate alert and reaction, such as, denial-of-service. | |
| Auditing | 100% monitoring and logging of queries and modifications by all tasks (including server side tasks), without loading the system, and without accessing the database. |
| Convenient tracking and searching of the contents of the recorded tasks. | |
| Monitoring & eporting | Saving of the records of all accesses to the database, and post-audit. |
| Utilization of analysis reports from various points of view of the real-time statistics of the logged data. | |
| Performance diagnosis based on data mining technique, and preventive measures for security violations. |
 |
�System
 |
�Benefits
|
Supported Platforms & Data Sheet
H/W Specification Chakra Hybrid for Enterprise Chakra GW FOR SMB |
|
Details of Feature
Chakra v2.1.3 vs Chakra v3.0.0
|
|
B2B Trade
| Price (FOB) | Negotiable | transportation | - |
|---|---|---|---|
| MOQ | Negotiable | Leadtime | Negotiable |
| Payment Options | Negotiable | Shipping time | Negotiable |

- President
- Samsoo Son
- Address
- 11fl, Samhwan Bldg., 98-5, Unni-dong, Jongno-gu, Seoul, 110-742, Korea
- Product Category
- Computer Software
- No. of Total Employees
- 1-50
- Company introduction
-
WareValley, Inc is privately held company, founded by former Oracle Korea management and engineering team in 2001. We have been focusing on developing innovative database related software and solutions which can help our customers manage and protect mission critical data in Oracle, and IBM, MS SQL, and Sybase environment.
Our company is headquartered in Seoul, Korea with distributors in Japan, where we are making noticeable market penetration in the first year. Our management team consists of proven top professionals with extensive technology and management experiences from Oracle, Siebel, and one of the most successful software start-up, E-Net Corp.
Currently, we are recognized as #1 database security / compliance Solution Company in Korea and our customer base is growing rapidly with a few top leading enterprises in Korea and Japan. Our customer lists include a few leading enterprises in diversified industry area, such as retail / institutional banking, government agency, manufacturing, healthcare, and one of the largest retail / home shopping companies.
Today's leading enterprises are facing with increasing internal / external threats to information security and strict regulatory environment, such as SOx (Sarbanes-Oxley), BASEL II, GLBA, HIPAA, and PCI. Our innovative market leading Database security / audit product, Chakra, is designed as core building block of IT infrastructure to prevent and manage information security issues with full auditing capability without affecting the database servers and infrastructure to meet those regulatory requirements, as well as to satisfy customers' own information security standard.
- Main Product
Related Products

RIMETALK - Enterprise Mobile Application with PTT function

Tayo the Little Bus (Animation)
OMV+

Document Security

Kobuki